WPScan 工具简单使用
WPScan 工具简单使用
- 最近在打 Vulnhub,正巧遇到了 Wordpress,想起以前用的一个工具 wpscan,做个记录吧。
- 本篇文章参考:
1 工具介绍
- WPScan 是一款用于 WordPress 网站的漏洞扫描和安全检测的开源工具。它是一个命令行工具,旨在帮助安全专家和网站管理员发现和修复可能存在的 WordPress 漏洞和安全问题。
- 以下是 WPScan 工具的一些主要特点和功能:
- 漏洞扫描:WPScan 可以扫描 WordPress 网站以查找已知漏洞和安全问题。它使用一个广泛的漏洞数据库来检测潜在的安全漏洞,包括已公开披露的漏洞、插件和主题的已知漏洞等。
- 用户名枚举:WPScan 可以尝试枚举 WordPress 网站的有效用户名。这可以帮助攻击者确定目标网站上存在的有效用户,从而进行更有针对性的攻击。
- 弱密码猜测:WPScan 可以进行弱密码猜测攻击,尝试使用常见的用户名和密码组合进行登录。这有助于检测使用弱密码的用户账户,从而提醒管理员采取更强的密码策略。
- 插件和主题扫描:WPScan 可以扫描已安装的 WordPress 插件和主题,以检测已知的漏洞和安全问题。这可以帮助管理员及时更新和修复存在问题的插件和主题,以减少潜在的安全风险。
- 数据库扫描:WPScan 可以检查 WordPress 数据库中的敏感信息,如数据库名、表前缀等。这有助于发现可能泄露敏感信息的配置问题。
2 工具安装
- WPScan 是 Kali Linux 默认自带的一款漏洞扫描工具,由于 Kali 中自带了 WPScan,所以怎么安装就不讲了,直接说说怎么使用:
1 | root at kali in ~/Desktop |
3 工具使用
3.1 常用参数
- 使用 wpscan -h 查看参数用法:
1 | root at kali in ~ |
3.1.1 扫描格式参数
| 参数名称 | 参数说明 |
|---|---|
| wpscan –url | 填写要扫描的 URL,允许使用 http / https,默认情况下是 http。 除非使用 update 参数,否则该选项是必须携带的。 |
| wpscan -h/–hh–version | 1. 用于显示简要的帮助信息,并在显示后退出 2. 用于显示完整的帮助信息,并在显示后退出 3. 用于显示工具的版本号,并在显示后退出 |
| wpscan -v/–[no-]banner | 1. 用于启用详细模式,通过使用该选项,wpscan 将输出更详细的信息和日志,以便您可以更全面地了解扫描的进展和结果。 2. 用于控制是否显示工具的 banner,默认情况下,该选项设置为 true,即显示 banner。 |
| wpscan -o | 用于将扫描结果输出到指定的文件中。 |
| wpscan -f | 用于指定输出结果的格式,您可以根据需要选择以下可用的格式选项: 1. cli-no-colour/cli-no-color:以无颜色的纯文本格式输出结果到终端。 2. json:以 JSON 格式输出结果。 3. cli:以带有颜色的文本格式输出结果到终端(默认选项)。 |
3.1.2 扫描指定参数
| 参数名称 | 参数说明 |
|---|---|
| wpscan –detection-mode | 用于指定检测模式。默认情况下,检测模式设置为 mixed,但您可以根据需要选择以下可用的选项: 1. mixed:混合模式,使用默认的综合检测策略。 2. passive:被动模式,仅进行被动检测,减少对目标网站的影响。 3. aggressive:积极模式,使用更积极的检测策略,可能会对目标网站产生更大的影响。 |
| wpscan –user-agent | 指定自定义的 User-Agent 标头,以模拟特定的用户代理 |
| wpscan –random-user-agent | 每次扫描使用一个随机的用户代理,以增加匿名性和多样性 |
| wpscan –http-auth login:password | 这个选项用于指定 HTTP 身份验证(HTTP Authentication)的用户名和密码,以便在扫描时进行身份验证。 |
| wpscan -t | 用于指定最大线程数。默认情况下,最大线程数设置为 5。您可以根据系统资源和性能需求调整该值。 |
| wpscan –throttle MilliSeconds | 用于指定在执行另一个网络请求之前等待的时间间隔(以毫秒为单位)。如果使用了这个选项,最大线程数将被设置为 1,以确保在发出连续请求之前有足够的延迟时间。 |
| wpscan –request-timeout | 指定请求的超时时间,以秒为单位。默认超时时间为 60 秒。如果在此时间内没有收到响应,请求将超时。 |
| wpscan –connect-timeout | 这个选项用于指定连接的超时时间,以秒为单位。默认连接超时时间为 30 秒。如果在此时间内无法建立连接,连接将超时。 |
| wpscan –disable-tls-checks | 这个选项用于禁用 SSL / TLS 证书验证,并降级到 TLS 1.0+。请注意,这需要 cURL 7.66 或更高版本支持。 |
| wpscan –proxy | 用于指定代理服务器的协议、IP 地址和端口号,以便通过代理进行扫描。 |
| wpscan –proxy-auth login:password | 这个选项用于指定代理服务器的身份验证用户名和密码。 |
| wpscan –cookie-string | 用于请求的 Cookie 字符串,您可以使用此选项将特定的 Cookie 值传递给扫描。 |
| wpscan –force | 用于强制执行扫描,即使目标网站未运行 WordPress 或返回 403 错误。 |
| wpscan –[no-]update | 用于控制是否更新 wpscan 的数据库,默认情况下,数据库会被更新。 |
| wpscan –api-token | 用于提供 WPScan API 令牌,以获取漏洞数据。 |
| wpscan –wp-content-dir | 用于指定自定义的 wp-content 目录路径 |
| wpscan –wp-plugins-dir | 用于指定自定义的插件目录路径 |
3.1.3 漏洞扫描参数
| 参数名称 | 参数说明 |
|---|---|
| wpscan -e | 用于执行枚举过程。枚举过程用于发现和获取有关目标 WordPress 网站上的插件、主题、备份文件以及其他相关信息。 您可以选择以下可用的枚举选项: vp:枚举存在漏洞的插件 ap:枚举所有插件 p:枚举常用插件 vt:枚举存在漏洞的主题 at:枚举所有主题 t:枚举常用主题 tt:枚举 Timthumbs 插件 cb:枚举配置文件备份 dbe:枚举数据库导出 u:枚举用户 ID 范围。例如,u1-5 将枚举 ID 为 1 至 5 的用户。如果未提供参数,默认范围为 1-10。 m:枚举媒体 ID 范围。例如,m1-15 将枚举 ID 为 1 至 15 的媒体文件。请注意,为了检测媒体文件,Permalink 设置必须设置为” Plain”。如果未提供参数,默认范围为 1-100。 您可以使用逗号作为值之间的分隔符,同时选择多个枚举选项。默认情况下,如果未提供参数,则选择枚举存在漏洞的插件、存在漏洞的主题、Timthumbs 插件、配置文件备份、数据库导出、用户 ID 范围和媒体 ID 范围。 请注意:不同组别中的选项是互斥的,只能选择组别中的一个选项。例如,只能选择 vp、ap 或 p 中的一个选项;只能选择 vt、at 或 t 中的一个选项。 |
| wpscan –plugins-detection | 用于指定插件枚举的模式。默认情况下,使用被动模式(passive)进行插件枚举。可以选择以下模式: mixed:混合模式,既使用被动模式又使用积极模式进行插件枚举。 passive:被动模式,使用较低的请求量进行插件枚举。 aggressive:积极模式,使用更高的请求量进行插件枚举。 |
| –plugins-version-detection | 用于指定插件版本检测的模式,也是上述三种模式。 |
3.1.4 暴力破解参数
| 参数名称 | 参数说明 |
|---|---|
| wpscan -P | 用于指定密码攻击期间要使用的密码列表。您可以提供一个文件路径,该文件包含要在密码攻击中使用的密码列表。如果没有提供 –username / s 选项,则会执行用户枚举。 |
| wpscan -U | 用于指定密码攻击期间要使用的用户名列表。您可以提供一个用户名列表,以在密码攻击中使用。 |
| wpscan –multicall-max-passwords | 用于指定每个请求中发送的最大密码数量(仅适用于 XMLRPC 多次调用)。默认情况下,最大密码数量为 500。 |
| wpscan –password-attack | 用于强制使用给定的攻击类型,而不是自动确定。如果目标 WordPress 版本低于 4.4,则 xmlrpc-multicall 攻击只能用于 wp-login 和 xmlrpc 之间的选择。您可以选择以下攻击类型: wp-login:使用 wp-login.php 页面进行密码攻击。 xmlrpc:使用 XMLRPC 接口进行密码攻击。 xmlrpc-multicall:使用 XMLRPC 多次调用接口进行密码攻击(仅适用于 WordPress 版本低于 4.4)。 |
| wpscan –login-uri | 如果登录页面与默认的/wp-login.php 不同,可以使用此选项指定登录页面的 URI。 |
| wpscan –stealthy | 这是一个别名选项,相当于同时使用–random-user-agent、–detection-mode passive 和–plugins-version-detection passive。它用于在密码攻击中以隐蔽模式执行扫描,包括使用随机用户代理、被动检测模式和被动插件版本检测。 |
3.2 使用示例
- 这里以 VulnHub 靶机的 DC-2 为例。
3.2.1 更新数据库
1 | root at kali in ~ |
3.2.2 扫描指定的站点
1 | root at kali in ~ |
3.2.3 使用 API Token 扫描
3.2.3.1 注册 API Token
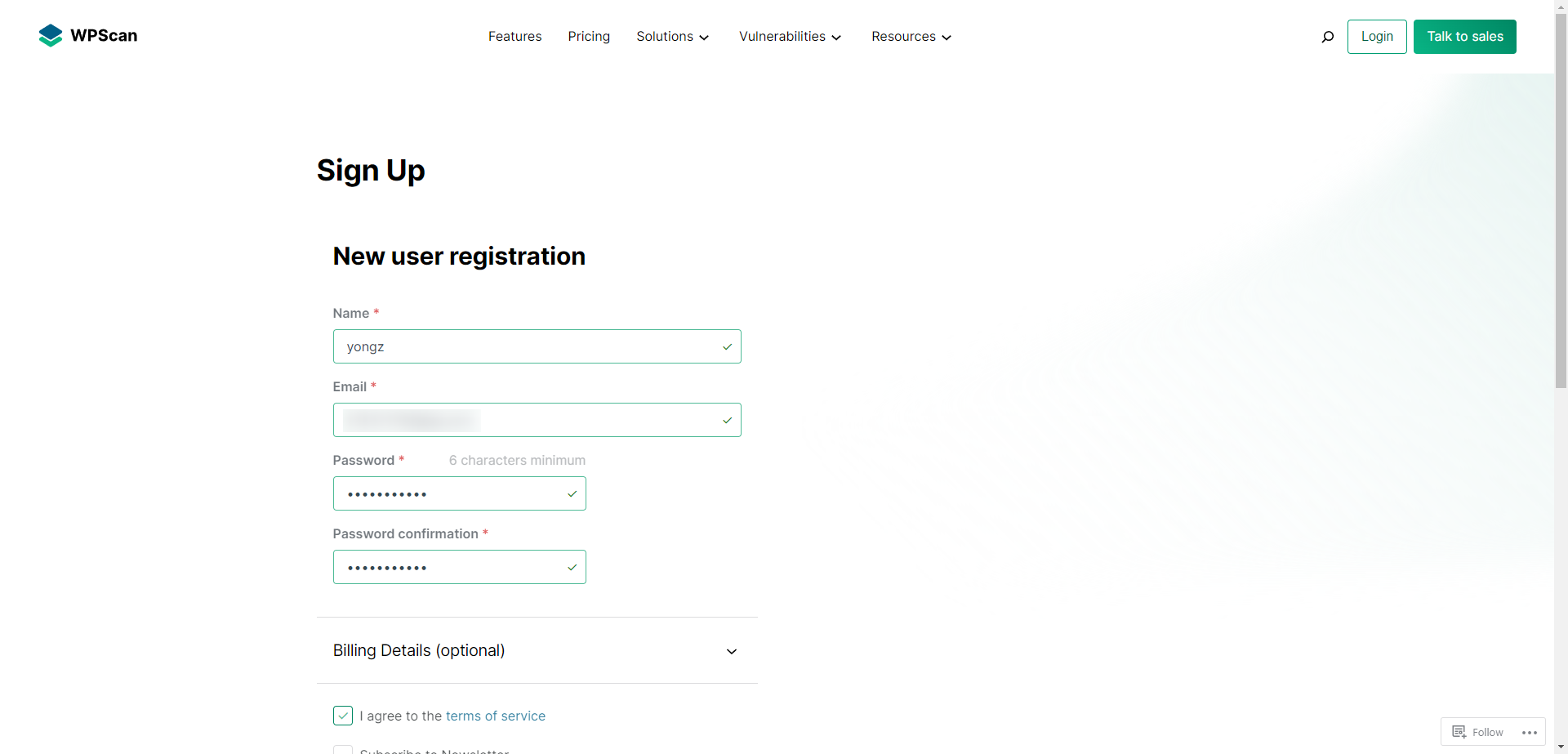
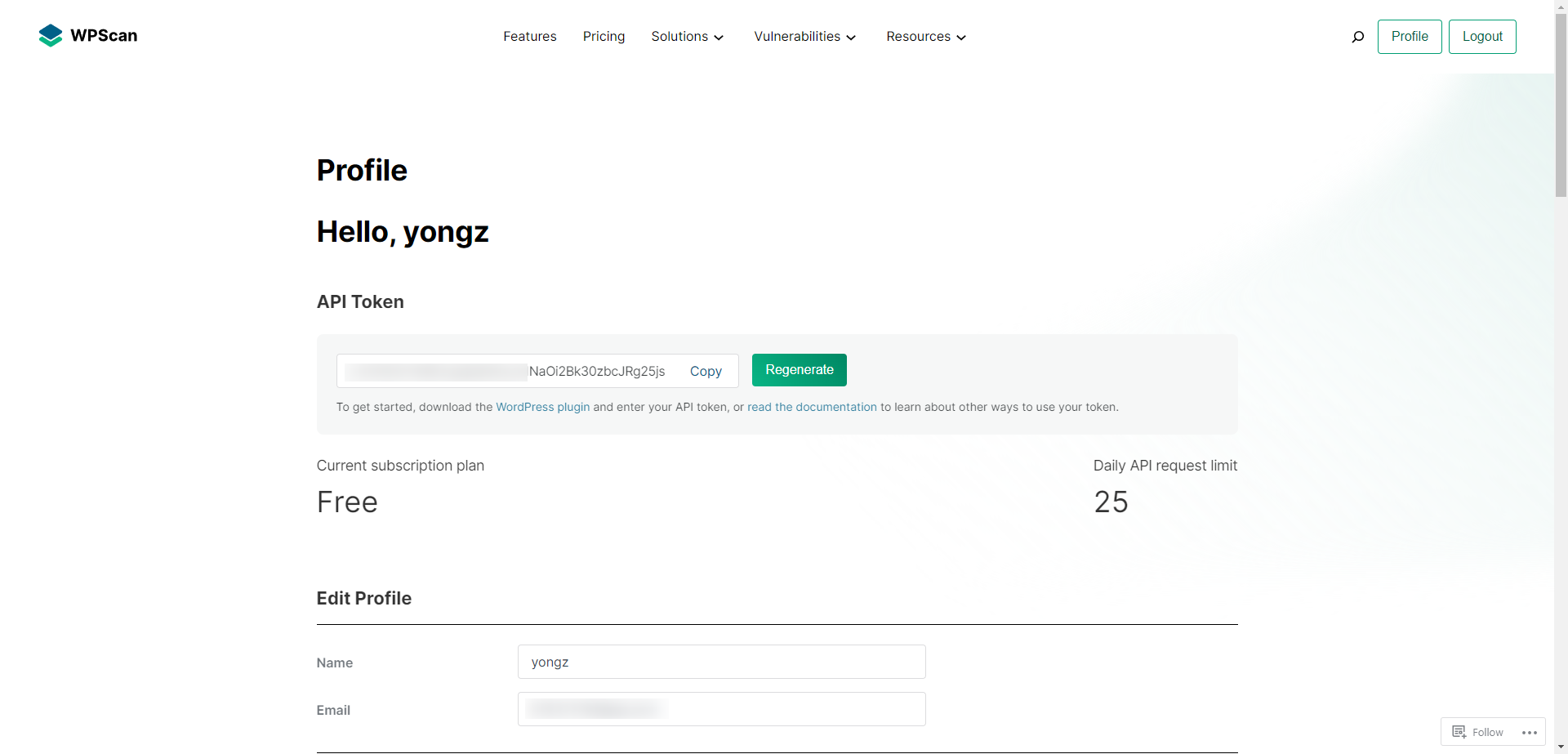
- 之后就可以使用 api 扫描漏洞了:
1 | root at kali in ~ |
3.2.4 扫描所有插件
1 | root at kali in ~ |
3.2.5 扫描所有主题
1 | root at kali in ~ |
3.2.6 枚举用户
1 | root at kali in ~ |
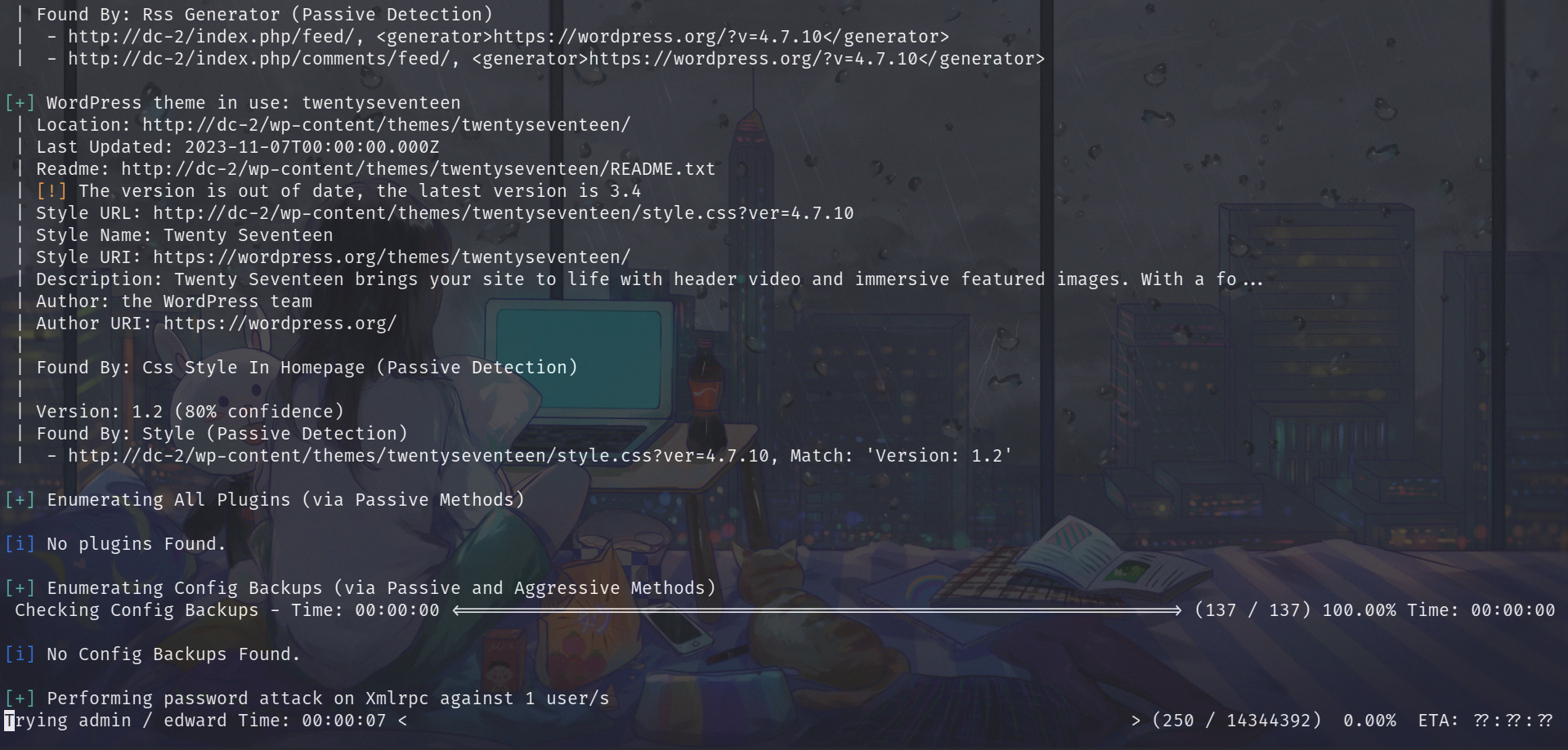
3.2.7 爆破密码
1 | root at kali in ~/Desktop |